Dec 20
31
TBT: New Year’s resolutions for cynics
I realize resolutions are supposed to be positive.[1] But a look at their lighter side may offer respite to those of us who are weary of feigning belief and encouragement each time we hear yet another “I’m going to lose weight” or “I’m going to give up [insert vice here].”
Here are a few of my favorite offbeat resolutions, curated from list after list boasting the “world’s funniest.” Speaking of which, I should resolve to lay off click-bait.
Wisdom from The New Yorker
You can hardly beat The New Yorker for insight and wit. The magazine’s Susanna Wolff advised:
Instead of preparing ambitious New Year’s resolutions like we did last year, let’s get ready for [the new year] by collectively aiming a little lower.
Wolff suggests that instead of resolving to learn a foreign language, for instance, “delete the Duolingo app from your phone and hope that ‘Storage Almost Full’ message stops popping up.” Why “spend more time with family” when you can “mute all of your family members on Facebook so that you can still tolerate spending time with them”? And in place of “drink less alcohol,” Wolff suggests “drink better alcohol.”
Here’s how legendary satirist Andy Borowitz’s pledge to quit smoking worked out:
On New Year’s Day, I started using nicotine patches, nicotine gum, and nicotine lozenges but stopped when I began to hallucinate that I was a Lucky Strike. January 2nd brought a new, less arrogant resolution: “I will smoke only cigarettes I did not pay for.”
In “This Is the Year,” Colin Nissan shows how specificity helps:
The more specific you are about your resolution, the better your chance of sticking with it. Don’t just say, “I want to lose weight.” Say, “When my arm jiggles, I want it to look less like a pelican’s throat-pouch choking down a bass.”
I shall resist further excerpting from The New Yorker for variety’s sake and to avoid tempting a reminder about infringement from their legal department.
Other voices
If you’re tired of saccharin-laden resolutions, you may like this, from James Agate: “To tolerate fools more gladly, provided this does not encourage them to take up more of my time.” Or this, from major league pitcher Dave Beard: “Many years ago I resolved never to bother with New Year’s resolutions, and I’ve stuck with it ever since.”
From the Twitterverse
Several collections of alleged all-time funniest tweeted resolutions cite these:
Just write out everything you did last night and at the beginning add the word “stop.” —@peteholmes
My New Years resolution is to be more assertive if that’s okay with you guys? —@megankcomedy
Here are a few more I enjoyed:
My New Year’s resolution is simply to remember to write 2021 instead of 2020. —@JiteshJain (Found on Buzzfeed)[2]
I am really unfit. Running for a train has almost done me in. A new years resolution of never running again I reckon —@SwtngTwtng (HelloGiggles)
I’ve read so many horrible things about drinking and smoking recently that I made a new, firm New Year’s resolution: NO MORE READING.” —@PhatOfficial (ScoopWhoop)
Encouragement from Mark Twain
It seems fitting to close on this one, from Mark Twain:
Now is the accepted time to make your regular annual good resolutions. Next week you can begin paving hell with them as usual.
Twain came up with that early in his career. It was published in an 1863 edition of Territorial Enterprise, a Virginia City, Nevada, newspaper. Oddly enough, he wasn’t much into tweeting.
[1] In an earlier post I wrote about the origin of New Year’s resolutions and listed some of the most common ones. Click here.
[2] I updated the years.
Odds are I’m not the first to observe that the year 2021 is slated to begin a few days hence. For pedants, that’s the real debut of the decade. Either way, I know I am but one of billions hoping 2021 will prove boring in comparison to 2020.
2020 has been a year of, shall we say, surprises: murder hornets, elections and election challenges (and not just in the United States), COVID-19 and all its consequences, hurricanes, wildfires, earthquakes, protests (some that turned dangerous), social issues, border crises, flooding, explosions, recession, unemployment, record heat, travel restrictions, record cold, a mysterious desert monolith in my home state of Utah …
… and just as we began to breathe a sigh of relief with January in our sights, along came venomous snake-infested sea foam rolling in over eastern Australian shores. For a more complete list of natural disasters, see Scientific American’s “A Running List of Record-Breaking Natural Disasters in 2020.” For a review of the year in financial matters, I commend you to Finextra’s Year in Review.
As the new year dawns, not a few of us will engage in the quaint, often well-intended, but futile exercise known as making New Years Resolutions. Year after year, the most popular resolutions have to do with weight loss, budgeting, and exercise.
Need help coming up with a resolution? A host of publications offer suggestions:
- Parade leads with “focus on a passion, not on the way you look.” (What if you’re passionate about the way you look?)
- Recommendation 56 out of 56 from Good Housekeeping is “make your home more fragrant.” (That would have been the ideal issue for a candle marketer ad.)
- CountryLiving would have you “write snail mail.” (Anyone remember what that is?)
- Lifehack’s number 25 out of 50 suggests, “Volunteer and give more to charity.” (I have nothing snarky to say about that one. It’s a great idea.)
The more cynical might enjoy this loophole-laden “solemnly professed” resolution from Ambrose Bierce’s The Unabridged Devil’s Dictionary, “suitably tempered so as not to place … goals for self-improvement beyond reach”:
I do hereby firmly resolve that during one year from date I will not drink any spirituous, vinous or malt liquors of any kind whatsoever, except in case I may think it would be a good thing to temporarily suspend this pledge. I will not utter a profane word—unless in sport—without having been previously vexed at something. I will make use of no tobacco in any of its forms, unless I think it would be kind of nice. I will not steal no more than I have actual use for. I will murder no one that does not offend me, except for his money. I will commit highway robbery upon none but small school children, and then only under the stimulus of present or prospective hunger. I will not bear false witness against my neighbor when nothing is to be made by it. I will be as moral and religious as the law shall compel me to be. I will run away with no man’s wife without her full and free consent, and never, no never, so help me heaven! will I take his children along. I won’t write any wicked slanders against anybody, unless by refraining I should sacrifice a good joke. I won’t whip any cripples, unless they come fooling about me when I am busy; and I will give all my roommates’ boots to the poor.
My best wishes to you. See you in 2021.
I shall open this week’s post by quoting Neal deGrasse Tyson. Tyson is a bestselling author, director of the Hayden Planetarium (part of the Department of Astrophysics at the American Museum of Natural History in New York), and, according to People magazine, the sexiest astrophysicist alive*.
But this post isn’t about astrophysics or sexiness. It’s about banking and bootstraps.
So, anyway, the quote. It’s from Tyson’s address to the University of Massachusetts graduating class of 2015:
It’s OK to encourage others to pull themselves up by their bootstraps. But just remember that some people have no boots.
What brought Tyson’s statement to mind this week was a recent Finextra article entitled, “HSBC offers homeless people bank accounts.” The article says that HSBC …
… is working with charities in the UK to help homeless people who do not have fixed addresses or photo IDs to open bank accounts, which can be managed in branches or online.
More than a wonderful thing to do, it’s a needful thing to do. Finextra continues:
… there are an estimated 320,000 homeless people in the UK, many of whom face financial exclusion because they do not have a fixed address or the appropriate ID needed to open bank accounts.
Backing up that claim was Business Insider, which recently observed, “Financial inclusion has been seen as key for reducing poverty.”
Thing is, if you need a banking relationship to exit poverty and you can’t get a bank account because you’re poor, you’re trapped in a vicious circle. You’re doomed to remain unbanked. Bootless, if you will.
So kudos to HSBC. They might just be offering a bootstrap to the homeless and others struggling with poverty.
In the United States, according to a report by the White House Council of Economic Advisers:
Over half a million people go homeless on a single night in the United States. Approximately 65 percent are found in homeless shelters, and the other 35 percent—just under 200,000—are found unsheltered on our streets (in places not intended for human habitation, such as sidewalks, parks, cars, or abandoned buildings).
Their estimate may be low, for homelessness is a moving target. According to the Urban Institute:
… over the course of a year at least 2.3 million and probably as many as 3.5 million people experience homelessness at least for a short period.
Out of the total U.S. population of 327 million, a half-million or even 3.5 million—about 0.153 and 1.07 percent, respectively—may not seem significant if you view them as cold, hard numbers instead of as people. All I can say is that the moment you imagine yourself or a loved one a member of that population, the number becomes considerably more significant.
The HSBC’s UK program may provide the homeless with “boots.” I’ll be eager for news of the program’s results over time. If a number of homeless grab that strap and use it to begin pulling themselves out of poverty, we in the U.S., indeed, the world, may have a worthy model to follow.
________________
* One wonders why People felt the need to qualify “sexiest astrophysicist” with “alive.” It’s hard to imagine a sexy deceased astrophysicist. It’s remarkable enough that there’s a living one.
Dec 20
21
Google’s tightened targeting rules may be for the best
In a move with serious marketing implications for the financial services industry, Google has revised its targeting policies for housing, employment, and credit.
Here is the latest from Google’s “Advertising Policies Help”:
In an effort to improve inclusivity for users disproportionately affected by societal biases; housing, employment, and credit products or services can no longer be targeted to audiences based on gender, age, parental status, marital status, or ZIP code.
With this policy change, setting aside the tech giant’s irresponsible use of a semicolon, Google is, as The Financial Brand put it,
… throwing a wrench into one of digital marketing’s biggest advantages—targeted ads. The search giant has long had policies in place barring ads targeting consumers based on identity, beliefs or sexuality, but this change drills to the core of what many financial institutions do with their digital campaigns: reach the person most likely to take out a loan or open an account with a highly relevant and timely message.
Google’s action isn’t entirely original. About a year earlier, Facebook arguably laid Google’s groundwork with its own, similarly “staggering” policy change, also reported by TFB.
Sticky wicket
Targeting has long been something of a sticky wicket in advertising. Properly approached, it is at once of benefit to marketers and consumers alike. For consumers, targeting reduces annoying clutter and increases the likelihood of receiving messages of interest. For marketers, as readers of this blog need no reminding, it is the key to crafting a relevant message and knowing where and how to deliver it. The most exquisitely crafted message is doomed to failure if it doesn’t appeal to and arrive in front of front of the right people. Case in point: I recently saw a beautifully executed promotion for a house painting service. It might have been quite successful—if the marketer hadn’t sent it almost exclusively to apartment dwellers.
Consumers voiced concerns about the use of their data long before the digital age. Hoping to preempt regulations, the Direct Mail Association (which later became the Direct Marketing Association, then the Data and Marketing Association, and is now the Association of National Advertisers) created and encouraged consumers to opt on to a national Do Not Mail List, and at the same time urged association members to honor it. But it’s a voluntary system, and consumers remain largely unaware of it, so it has done little assuage concerns.
The information consumers gave up in the old analog days pales in comparison to what they give up—and to what marketers silently capture—in the modern digital age. Name, address, and product choices? That’s kid stuff. If consumers were horrified to learn that ordering a jacket by mail from LL Bean put them on mailing lists available to other marketers, imagine their discomfort if they understood that digital billboards register their smartphones as they drive by, ready to correlate their trip with nearby purchases they may make. Big data is a PR nightmare always at the ready to explode.
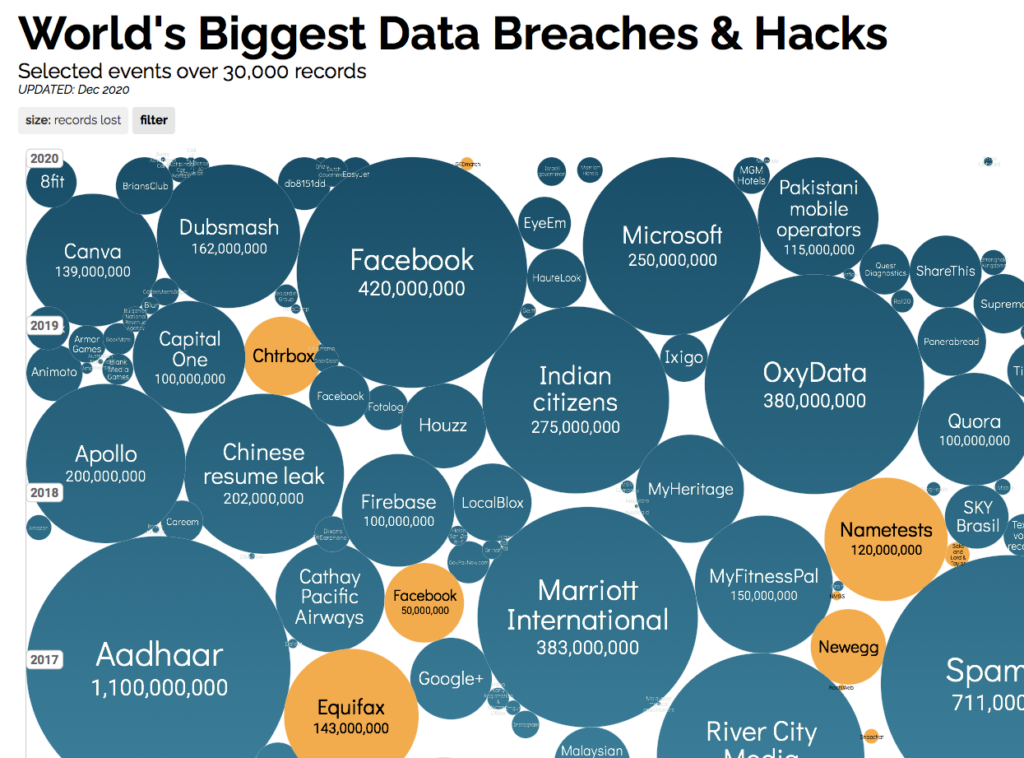
While the distinction between managing masses of data and spying on individuals is generally lost on consumers, marketers’ use of their information is only part of the concern. Consumers also worry about data gleaned by honorable companies only to be hacked by the not-so-honorable. Their concern is not without reason, as this chart from InformationIsBeauitful.net drives home.
Fairness
But let’s return to Google’s stated reason for the policy change: “In an effort to improve inclusivity for users disproportionately affected by societal biases …”
As reasons go, that one has legs. AI is not immune to GIGO. Targeting by gender, age, parental status, marital status, and ZIP code can inadvertently keep scales tilted against traditionally discriminated-against populations, contributing to a downward spiral based on associations and correlations that should have no bearing on what opportunities are extended to whom.
Google’s policy will mean financial marketers will have to work harder. But that’s the thing about fairness. It doesn’t come without work. This policy change isn’t necessarily a bad thing.
Dec 20
17
TBT: Just in time for that impossible to shop-for person in your life
Can’t come up with the right gift? These offbeat services probably won’t help. (But they’re funny.) Originally posted December 23, 2019.
You’ll recall that online merchants pulled in $7.4 billion in sales on the day following Thanksgiving. Biggest online Black Friday to date.
Thanks to Fiserv’s 2019 SpendTrend® Holiday Snapshot, we now know a bit more. For instance, “…spending via mobile wallets increased more than 80%, as consumers continue adopting new payment methods.” Also: “Black Friday brick-and-mortar sales were up 4.2%, with the greatest increase over normal shopping activity seen across electronics and appliances, sporting goods, and clothing/shoe stores. Electronics and appliance stores saw the largest average ticket size at $214 per transaction.”
PYMTS.com tells us that about 20 percent of this year’s Black Friday shoppers shopped only online. And Millennials spent “… an average of $509.50 on Black Friday … compared to an average of just $382.40 in 2018.” It reported in a separate article, “Cyber Monday is tracking to break eCommerce records and possibly go down in history as the biggest day ever for online sales in the U.S., The Financial Times (FT) reported on Sunday (Dec. 1).”
Besides the fact that I make my living in the digital payments industry, I am deeply grateful for technology that spares my wife and me from having to visit store after store to shop for our three children.
In fact, thanks to creative digital entrepreneurs, now you don’t even have to take your kids to the mall to see Santa. They can FaceTime him with services like TalkToSanta.com and VideoChatWithSanta.com. “It’s basically a webinar for your preteens,” quipped “Wait Wait Don’t Tell Me” host Peter Sagal last week. (But I’m not necessarily recommending it, especially after hearing panelist Faith Salie reply, “I watched some of these online, and the quality of the Santas, let’s just say, is variable.”)
Virtual Santas made me wonder what other offbeat services the digital revolution has dropped at our feet of late. So I decided to dig a little. Here’s what I found, just in time for the holidays.
Listverse names “Top 10 Bizarre Services You Can Buy Online.” One such is breakupshop.com, which offers to handle a romantic breakup on your behalf via text or email. I give them branding props, for “breakupshop” certainly has more appeal than, say, “helpforwimps.” (Which—attention entrepreneurs—is still available as of this writing.)
Perhaps the antithesis is InvisibleGirlFriend.com, which lets you create your own, virtual, online girlfriend. “You can then interact with them via text message. And yes, we have real humans playing your girlfriend on the other side.”
Romance challenges seem to be a favorite. Dirty Rotten Flowers will send a bouquet of dead, rotting flowers to the person of your choice. I’m sure they’re nice people, but I’m not recommending that one, either.
It’s a wonder that humankind survived until now without a service like PotatoParcel.com, “… a Shark Tank-featured company that allows you to send a personalized message to anyone you like on a potato.”
Under “Get The Best Weird Services,” fiverr.com lists a number of curious services you can obtain online. For $10, you can have someone “… yell your name at a bunch of yuppie golfers.” One fellow offers to “eat a peeled lemon and send you a video of it.” And here’s a sure winner: “I will make a bad drawing for you.”
Planning on being raptured? Wired describes a service that for “… just $40 a year” lets believers “arrange for up to 62 people to get a final message exactly six days after the Rapture.”
Oddee lists “12 Strangest Services,” and “strangest” is no exaggeration. “I will eat a handful of dry cat food for $5,” offers one contender for your money. Hard as that may be to resist, perhaps you’d prefer to pay a fellow to do jumping jacks while wearing a chicken outfit. Or you might wish to retain the services of someone who will take your verbal abuse. “Here’s your chance to express your thoughts in the most vulgar, nasty, and unapologetic way possible,” says the seller. “Hit me where it hurts … for five minutes over the phone.”
If in your quest for the perfect, last-minute gift you resort to any of the above, please note that I cannot be responsible for any consequences.